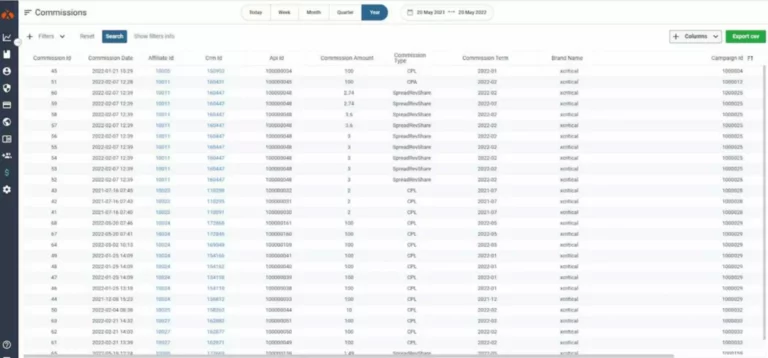
Deciding which type of wallet to use is dependent upon a variety of factors, including the frequency during which you trade, the price range allotted to your crypto wallet, and the distinctive options of the wallet. Cryptocurrency transactions are irreversible, so accuracy is paramount. Double-check recipient addresses by copying and pasting them rigorously https://www.xcritical.com/, and confirm the primary and last few characters. Be aware of tackle poisoning scams, where scammers send small quantities to your tackle to insert their tackle into your transaction historical past. All The Time use addresses from trusted sources, not just recent transaction lists. Earlier Than implementing security measures, it’s essential to grasp the potential dangers inherent in the crypto ecosystem.
For occasion, some hackers approached Dominic Lacovone as Apple Support. They tricked him into giving them entry to his iCloud account, where he saved his MetaMask recovery phrase. Although this would possibly sound stunning, a really helpful place to retailer your personal key would be your bank’s secure. Of course, this should only be a backup – you should all the time have entry to your non-public keys at your comfort. In continuation of the above, it’s important to maneuver your cryptocurrency out of a device that wants servicing.
There are varied forms of crypto wallets, and most of them may be accessed through a seed phrase, crucial component of your wallet. In the decentralized world of blockchain expertise, the most secure and most effective way to maintain crypto belongings is by utilizing a cold wallet, also called a hardware or offline wallet. This specialised electronic gadget shops the private key of a crypto wallet offline, making it troublesome for hackers to attack and guaranteeing the safety of your crypto assets.
Secure Your Devices
The ongoing evolution of cryptocurrency and cybersecurity applied sciences highlight the constant cat-and-mouse game between innovators and malicious actors within the digital monetary panorama. A crypto pockets is usually a bodily gadget or online platform that retains your non-public and public keys so you possibly can carry out transactions. You can ship crypto out of your pockets and use its tackle to receive crypto.
Utilizing a Digital Personal Community (VPN) encrypts your web site visitors, making it more durable for attackers to intercept data. Use trusted VPN companies, especially when accessing sensitive accounts. A cursory glance at the historic worth of bitcoin is sufficient to see massive peaks and troughs all through its lifespan. These dramatic swings in worth aren’t regular compared to the tempo crypto wallet security at which most mainstream belongings — like shares, exchange-traded funds (EFTs) and different kinds of equities — move in value. The FBI says it received over 69,000 public complaints about monetary fraud relating to cryptocurrency similar to bitcoin, ether or tether in 2023. And though these comprised simply 10% of the whole number of financial fraud complaints to the Bureau, they accounted for nearly half of complete losses, or $5.6 billion for the yr.
That’s why it’s critical by no means to go to web sites you don’t trust or that are outside the scope of your computer’s protection. Double- and triple-check the functions that you simply obtain and be 100 percent sure that they are the official ones and never pretend. Nevertheless, after you’ve done that, there are many things you are in a position to do to guarantee the protection of your Bitcoin and other cryptocurrencies.
When creating a pockets, whether or not it is a cold or hot pockets, most Web3 pockets applications require users to put in writing down a restoration phrase. This handwritten restoration phrase helps users get well their wallet in case of any issues and can also be necessary to recover the crypto wallet in other functions. Crypto wallets are important for anyone who desires to buy, personal or promote crypto. Your pockets shops your private and public keys and interacts with different blockchains to permit you to securely send and obtain digital assets Cryptocurrency wallet.
Secure Your Bitcoin: High Secure Storage Methods
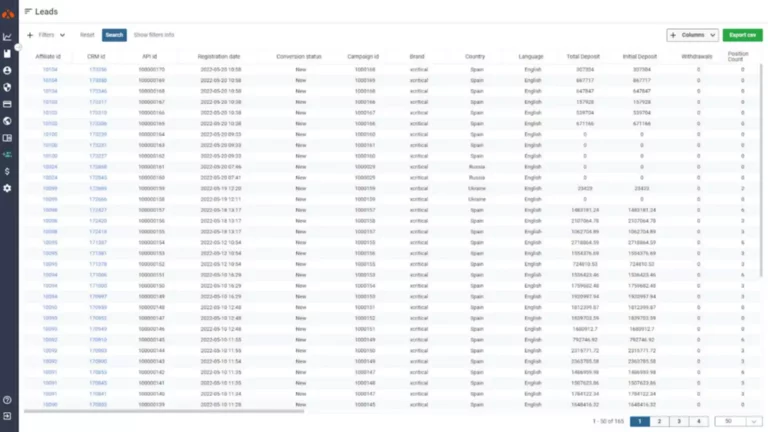
Are you concerned about the rising number of hacking incidents and security breaches in the cryptocurrency world? Do you are worried that somebody may gain unauthorized access to your crypto assets? Let’s discover the best strategies to guard your crypto holdings. When you purchase bitcoin, you’re given possession of the quantity you bought. You’re given two keys—one is your public key, the other is private.
Bitcoin Value Maintains $93k, Ethereum Hits 3-week High: Market Watch
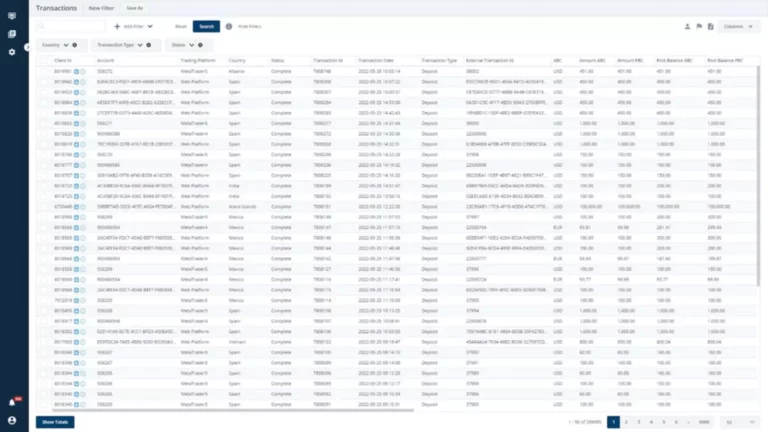
Instead, they get stored in pockets information or managed by crypto wallet apps. This “one-way” — or “trap-door” — encryption, makes it potential to share a public key with out worry that someone will figure out your personal key and steal your crypto. In the decentralized world, how can you handle your crypto assets?
Greatest Cybersecurity Practices For Cellular App Developers Implementing Crypto Wallets
- They forestall unauthorized transactions even when one personal secret is compromised.
- You must also be conversant in their video games and be on the lookout for them.
- Of course, chilly wallets can nonetheless be stolen or misplaced, and you can forget tips on how to access them.
- Keeping your investments secure is essential, particularly given the rise in cryptocurrency hacks.
Unlike an everyday wallet, a crypto wallet doesn’t truly hold your belongings. Instead, it stores credentials known as non-public keys that provide you with entry to your belongings on the blockchain. Nonetheless, as a end result of they’re connected to the web, scorching wallets are extra susceptible to hacking and theft.